Carding Course: A Complete Guide
What is Carding?
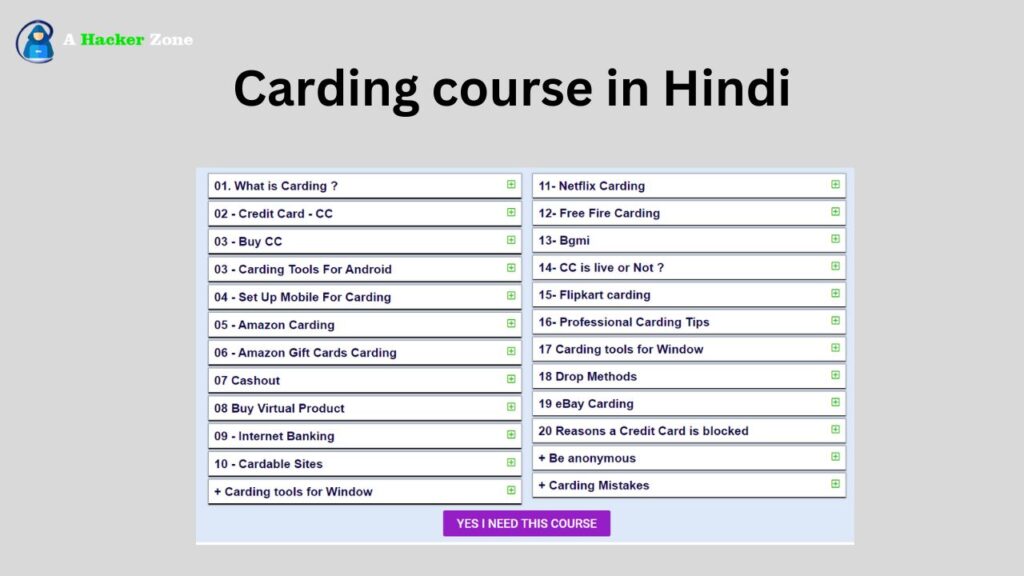
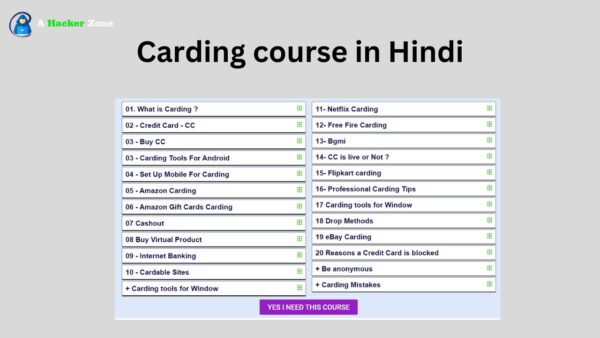
Full Carding course: Carding is when someone uses a stolen or fake credit card number to buy things without permission. Carding’s main goal is to get things or services by using stolen credit card information. This illegal behavior involves messing with financial systems and getting around security measures that are meant to stop scams.
Learn More:
Contact us: @Support
Contact us If You Need any Help >>>Click here
Full Carding course
Advance Carding Course
Do you want to learn carding from basic to advanced? If yes, then enroll in the Advance Carding Course
Join our Team as a Member For Lifetime.
If you have any questions regarding carding, contact us we will help you. and guide you. I hope the Carding Forums Blog was helpful to you.
Techniques and Tools
People often refer to credit card fraud as “carding,” but to gain a deeper understanding of its technical aspects, you must understand the various tools, techniques, and methods involved. This complete lesson on carding will teach you everything you need to know, from how credit card systems work to more advanced carding skills and safety measures.
Carding is wrong and against the law, but knowing how it works can help cybersecurity experts, scholars, and people who want to keep their banking information safe from fraud. In this blog, we’ll cover everything from card basics to advanced moves.
Understanding Credit Cards (CC)
It’s important to know how credit cards work in general before you start carding. Credit cards, or CCs, let people borrow money from banks and other financial institutions to buy things. The card has a CVV code, a unique number, and an expiration date that you need to keep secret.
Full Carding course
Credit cards have different benefits, like credit limits, interest rates, and ways to earn rewards. A lot of people pay their bills, shop online, and do other things with these cards. On the other hand, crooks often go after them to steal cards.
Buying Credit Cards (CC)
One of the primary techniques used in carding involves acquiring credit card details (CC) illegally. These stolen credit card numbers are often sold on the dark web or through underground forums. The purchased credit cards typically contain the cardholder’s name, card number, expiration date, and CVV code, all of which are essential for conducting fraudulent transactions.
The process of purchasing CC from unauthorized sources is risky and often leads to severe legal consequences. However, for cybersecurity experts, understanding how criminals acquire such data helps develop better protective measures.
Carding Tools for Android
People don’t just card on computers anymore; mobile devices, especially Android smartphones, have become important places to do carding. Credit card makers, spoofing tools, and proxy services are just a few of the carding tools that Android users can use to make it easier to commit theft.
Fraudsters can use these tools to make fake transactions look real, hide their names, and get around carding websites’ security checks. Some Android apps can even handle the process of carding, which makes it go faster.
Setting Up Your Mobile Device for Carding
Setting up your mobile device for carding involves several steps, such as installing the right tools and ensuring your device remains anonymous. The following measures are crucial for preparing your Android mobile for carding:
- Install VPNs: Use VPN services to hide your IP address and encrypt your internet traffic, making it difficult for authorities to trace the source of fraudulent activities.
- Use proxy servers: proxy services help mask your real location, further securing your anonymity during transactions.
- Carding Apps: Install specific carding apps that facilitate the use of stolen card details. These apps may come with built-in tools to automate various aspects of the process.
Amazon Carding
Amazon is one of the most popular e-commerce platforms, making it a frequent target for carding attacks. Amazon carding involves using stolen or fake credit card information to make unauthorized purchases on Amazon.
Fraudsters may exploit Amazon’s security loopholes to bypass payment verification processes. Some may even use gift cards to launder money or purchase high-demand products like electronics to resell for a profit.
To protect yourself from Amazon carding, it’s essential to use secure payment methods like 2FA (Two-Factor Authentication), monitor transaction history closely, and enable notifications for any account activity.
Amazon Gift Cards Carding
Amazon gift card carding is a variant of Amazon carding where criminals use stolen credit card data to buy Amazon gift cards. Criminals use these cards to make purchases or sell them for cash on the black market.
Full Carding course
Gift cards offer a relatively safe method for fraudsters to avoid detection, as they are less traceable than direct purchases made with stolen credit cards. The carding community frequently exploits this by targeting vulnerable accounts or using bots to generate large numbers of gift cards.
Cashout Methods
Cashout is the process of converting the fraudulent purchases into real money. After conducting carding activities, fraudsters use cashout techniques to monetize stolen goods or services. Common cashout methods include:
- Reselling Products: Fraudsters often resell the stolen goods on black markets or e-commerce platforms like eBay or Craigslist.
- Bitcoin: Many prefer converting the proceeds into cryptocurrency, particularly Bitcoin, as it offers a higher level of anonymity.
- Money Laundering: One may use money laundering techniques to conceal the funds’ origins.
Buying Virtual Products Using Stolen Credit Cards
In the world of carding, virtual products such as game credits, subscriptions, or software are highly sought after. Fraudsters often use stolen credit card details to purchase these virtual goods. Once acquired, they can either resell them for cash or use them for personal gain. Virtual products have a lower risk of detection since they don’t require physical delivery, making them an attractive target for carding.
Internet Banking and Carding
Internet banking plays a crucial role in carding activities, as it provides fraudsters with direct access to funds. Many carding tools are designed to bypass banking security protocols, allowing criminals to access and transfer money quickly.
Cybercriminals use bank account hijacking techniques to gain unauthorized access to victims’ online bank accounts, making it easier for them to siphon off funds or purchase goods directly.
Cardable Sites for Carding
Cardable sites—websites vulnerable to fraud or with weak security measures—are typically the target of carding. These sites often include e-commerce platforms, subscription services, or online stores where users can purchase items or services using stolen credit card details.
Identifying cardable sites is essential for cybercriminals, as it helps them target platforms that are more likely to accept fraudulent transactions without triggering security alerts.
Netflix Carding
One of the most popular forms of carding is Netflix carding. Fraudsters use stolen credit card details to sign up for Netflix accounts, often using stolen accounts for free access or reselling them on the dark web. Netflix carding typically involves bypassing verification processes and exploiting user account weaknesses.
Free Fire and BGMI Carding
Carders frequently target popular online multiplayer games like Free Fire and BGMI (Battlegrounds Mobile India). Fraudsters frequently employ carding techniques to buy in-game currency and items, which they can then resell or utilize to obtain an unfair advantage in the game.
Checking if a Credit Card is Live or Not
Determining whether a credit card is live or not is essential for carding activities. A live card refers to a valid card that has not been flagged or blocked by the bank. Fraudsters use specific tools to check whether a credit card is still active and capable of completing fraudulent transactions. Full Carding course
Flipkart Carding
Similar to Amazon, carders have targeted Flipkart, a major e-commerce platform in India. Flipkart carding involves using stolen credit card details to make purchases on Flipkart, typically through fake or compromised accounts.
Professional Carding Tips
Professional carders have honed their skills over time, employing advanced tools and techniques to execute successful carding operations. Key tips for advanced carding include:
- Use Multiple Proxies: Never use the same proxy for multiple transactions to avoid detection.
- Automate Processes: Tools like bots can automate many aspects of the carding process, including checking card validity and making purchases.
- Minimize Mistakes: Carefully plan every action, as carding errors can result in account bans or arrests.
Carding Tools for Windows
Cybercriminals often use Android devices for carding, but they also rely on Windows-based tools for their operations. These tools range from credit card generators to proxy software and automated bots that help streamline the carding process.
Drop Methods
Carders utilize the drop method to evade detection when using stolen credit card information. It involves using third-party addresses (called drops) to receive goods and services purchased with fraudulently obtained cards. Drops enable carders to conceal their identity and prevent direct connections to the fraudulent activity.
eBay Carding
eBay carding is another variant where fraudsters use stolen credit card details to purchase items on eBay. These products are often resold or laundered through other platforms. eBay’s large marketplace makes it a prime target for carders looking to exploit vulnerabilities in payment systems.
Why Credit Cards Get Blocked
Full Carding course: There are several reasons why a credit card may get blocked:
- Suspicious Transactions: Unusual activity or transactions that don’t match the user’s spending pattern can trigger a block.
- Multiple Failed Attempts: Too many failed attempts to make a purchase can also result in a card being flagged.
- Reporting of Fraud: If the cardholder reports their card as stolen or compromised, it. carding course free download
Carding Course
Learn More:
Contact us: @Support
Contact us If You Need any Help >>>Click here
Advance Carding Course
Do you want to learn carding from basic to advanced? If yes, then Enroll Advance Carding Course
Join our Team as a Member For Life time
If you have any Question regarding carding contact us we will help you. and guide you. > I hope carding forums Blog helped you.


Reviews
There are no reviews yet.